.jpg)
Contact Us
info@cambodiasoft.com
Contact Us
# Products
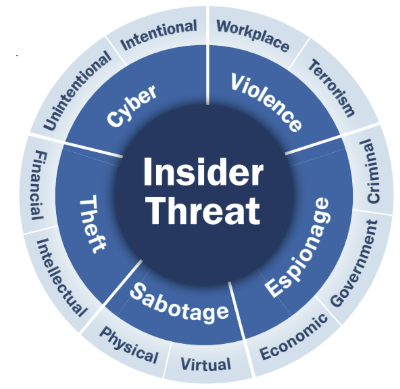
Insider Threat Management
Insider Threat Management is designed to identify, monitor, and mitigate threats that originate from within your organization. Insider threats can come from employees, contractors, or business partners with legitimate access to your systems, but who may misuse their access intentionally or unintentionally. Our solutions provide comprehensive tools to monitor user behavior, detect suspicious activities, and enforce security policies to prevent data breaches, fraud, and other malicious actions from within.
- User and Entity Behavior Analytics (UEBA) : Uses machine learning to analyze user behavior patterns and detect anomalies that may indicate a potential insider threat, such as unusual login times, data access patterns, or large file transfers.
- Risk Scoring : Assigns risk scores to users based on their behavior, role, and access levels, allowing you to prioritize monitoring and response efforts for high-risk individuals.
- Real-Time Alerts and Notifications : Triggers immediate alerts for suspicious activities, enabling security teams to investigate and respond before any damage is done.
- Data Loss Prevention (DLP) : Monitors and controls the movement of sensitive data within your organization, preventing unauthorized sharing or exfiltration of critical information.
- Policy Enforcement : Automatically enforces security policies that limit access to sensitive data and systems based on user roles and activities, reducing the risk of insider threats.