.jpg)
Contact Us
info@cambodiasoft.com
Contact Us
# Products
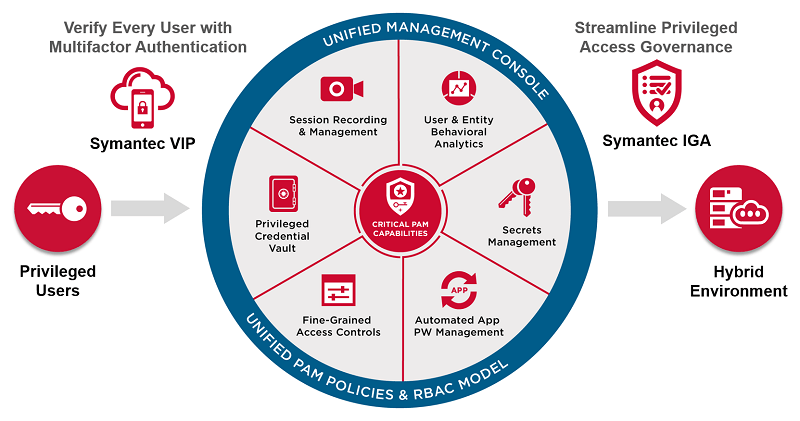
Privileged Access Management (PAM)
Privileged Access Management (PAM) is critical for securing high-level access within your organization. Privileged accounts—such as those used by administrators, executives, and IT personnel—hold the keys to your most critical systems and data. Without proper management, these accounts can become a significant vulnerability, either through external compromise or misuse by insiders. Our PAM solutions offer a secure, streamlined way to manage privileged access, ensuring that only authorized users can access sensitive resources.
- Credential Vaulting : Securely stores and manages privileged account credentials, ensuring that they are only accessible by authorized users. Automated password rotation and vaulting reduce the risk of static credentials being compromised.
- Granular Access Control : Define detailed access policies that dictate who can access what resources, when, and for what purpose. Enforce least privilege principles to minimize the risk of misuse.
- Session Recording and Monitoring : Record all privileged sessions, providing a full audit trail of activities performed during these sessions. This helps in identifying and addressing any suspicious or unauthorized actions.
- Just-In-Time Access : Grant temporary, time-limited access to critical systems only when necessary, reducing the exposure of privileged accounts.
- Audit and Compliance Reporting : Generate detailed reports on privileged access activities to meet regulatory requirements and support internal audits.